How Secure is Your Password? Essential Tips for Enhancing Your Password Security

How long has it been since you last tried to log into an account, only to realize you have forgotten your password? By the time you reset it, you probably forgot what you were doing there in the first place.
Setting, resetting, remembering, and managing passwords, PIN codes, and passphrases can be exasperating. With all these (not so) little annoyances building over time, one might wonder: do passwords exist just to make our lives difficult?
Today we are cracking the code on password security, with a little help from our cybersecurity experts. Let's first see why passwords are fundamental to your online privacy and security:
"You have to understand that roughly 60% - if not more - of all high-profile breaches in the past five years alone happened because of password reuse.
Attackers figured out what password victims used for a specific website and then tried that password on other websites like email, cloud storage, social media, or corporate accounts. And, unfortunately, it worked."
Alex "Jay" Balan (Director of Security Research, Bitdefender)
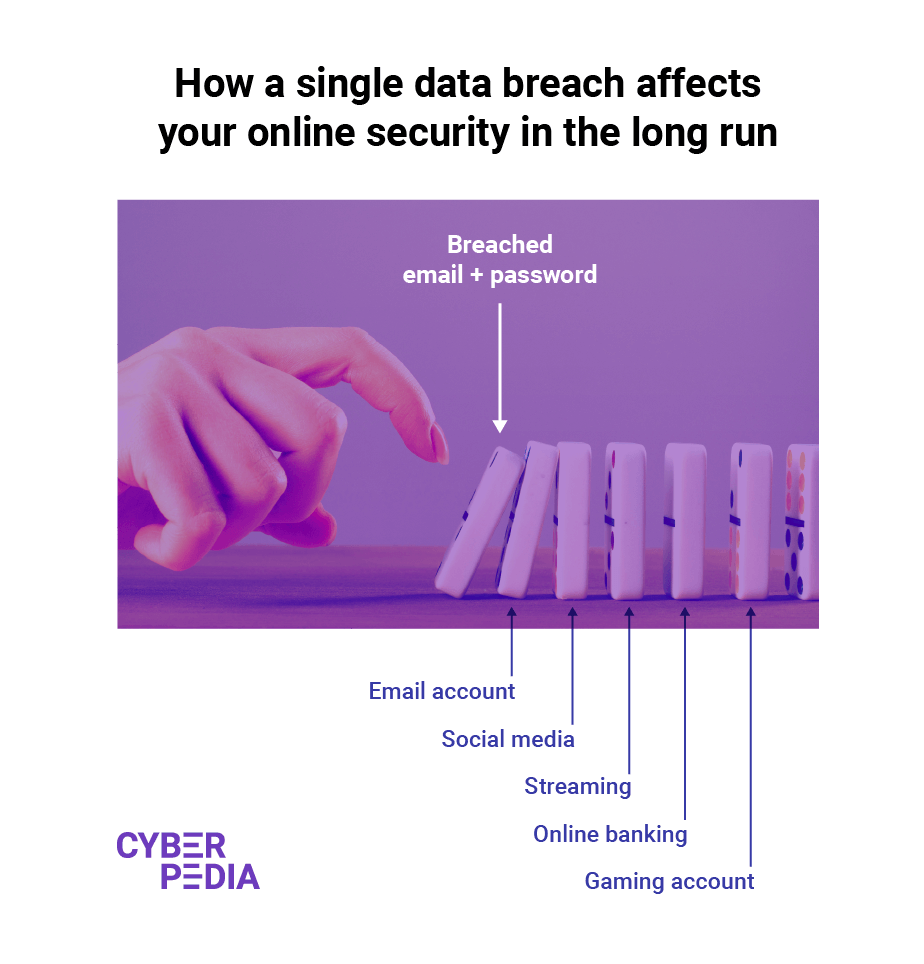
Why is Password Security Important?
Passwords protect your data, finances and confidential information from unauthorized access. They are the key to the "vaults" that store your information in the digital world and one of the main layers of security across your entire Internet activity.
This type of security tool has been in use for a long time. Today, it remains one of the core mechanisms to validate your identity in systems that require authorization before granting access to protected information, services, and products.
The username-password combination is one of the most widespread means of securing secret data and it has been serving us well since the early 1960’s, when it was first introduced. However, in recent years, passwords have become a burden for most Internet users, adding friction to their lives as their digital footprint rapidly expands.
Nowadays, every Internet user juggles dozens, if not hundreds, of passwords. And because they are so commonly used, this can make you overlook the critical role passwords play in protecting your personal information from being exposed online.
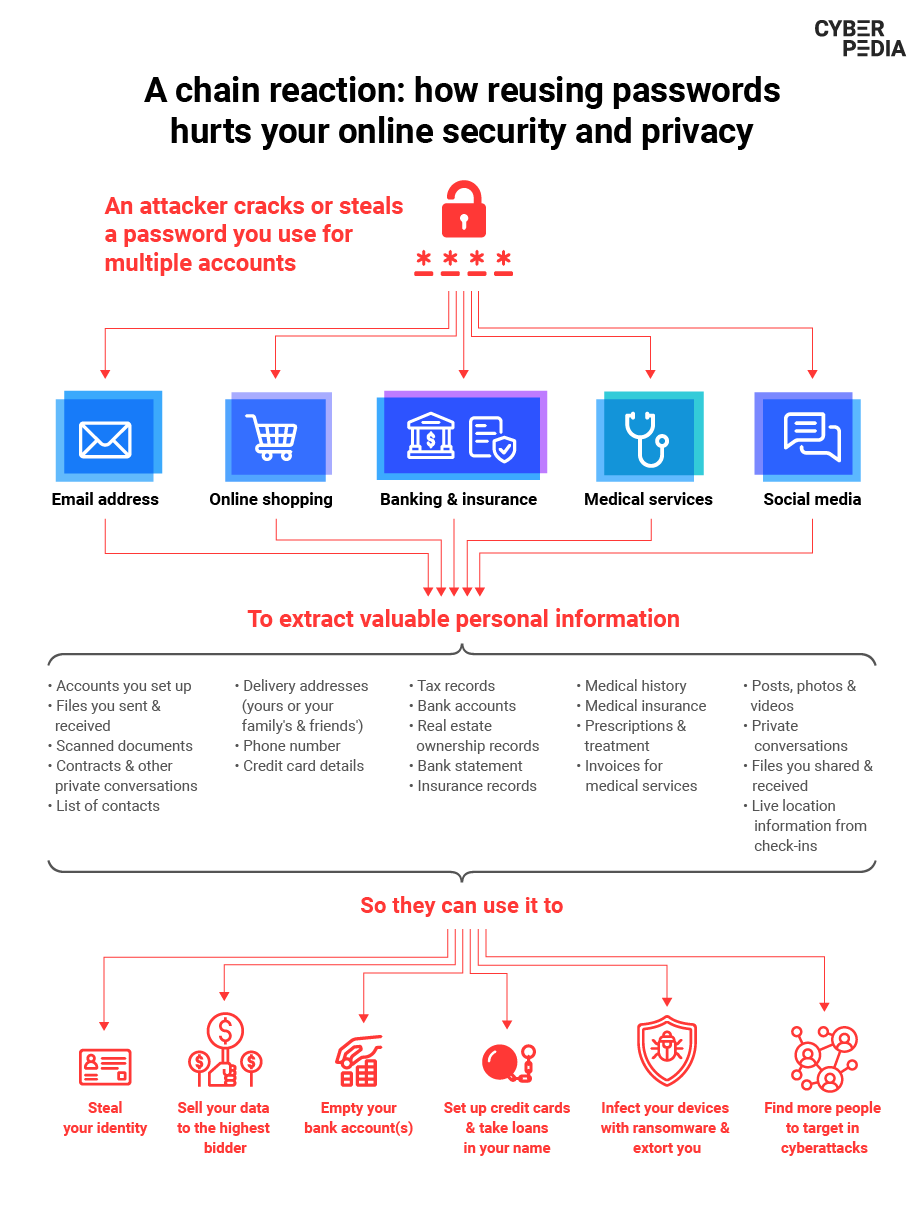
Each password that cyber-criminals manage to steal creates more and more breaches in your security. Although organizations can have robust data security protocols in place, you are protected only if you use strong passwords for your accounts. A cyber-attacker or scammer can gain access to your account and your data by tricking the system into thinking you are the one trying to log in.
Fortunately, some systems can detect suspicious activity by flagging unusual patterns that differ from your typical user behavior: increased volume of login attempts, sign-ins from remote locations far from your usual areas, or high levels of account activity.
Is a Password Considered PII (Personally Identifiable Information)?
Most definitely. A password, just like your name, social security number, driver's license, bank account, and credit or debit card numbers, is a key type of personal identifiable information.
"By all means, yes! The law says that a password is a piece of personally identifiable information, since you use it to identify against the service."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
That means that your passwords are protected under laws and regulations such as the General Data Protection Regulation (GDPR) in Europe and the California Online Privacy Protection Act (OPPA) of 2003 in the United States.
Common Techniques Used for Cracking Passwords
Let's take a closer look at the five main password-cracking tactics and the vulnerabilities they exploit:
Brute-force attack
Cyber-criminals feed passwords leaked from data breaches and relevant clues into an automated system that methodically checks all possible combinations until they find a match. The more passwords the targeted individual reuses, the more extensive the damage is when the password gets cracked.
There are many variations of this tactic, including the password spraying attack, where attackers try the same password against multiple accounts at once to avoid getting locked out.
Dictionary attack
Besides the most common passwords and word combinations, this attack also uses all the words in the dictionary (not just in English, but also in various other languages) to guess a victim’s credentials. People often use familiar words strung together, which makes this type of attack particularly effective.
Rainbow table attack
This attack is based on data that cyber-criminals have already managed to extract. They keep records of passwords and their corresponding hashes, so they can decode and crack encrypted passwords by using this information.
Phishing
The most common password-cracking technique is to trick people into submitting their username and password to a fake website that mimics a legitimate one. Attackers can see the passwords as the unsuspecting users type them in, which means they can immediately use the compromised credentials to gain unauthorized access.
Social engineering
Cyber-attackers attempt to extract passwords from their victims by posing as a credible figure - be it a supervisor, coworker, friend, or even a relative.
"On a single computer graphics card, cyber-criminals can attempt billions of password combinations per second.
They also employ predefined techniques to try to generate passwords that relate to somebody's identity.
They feed the program with hints about the victim’s name, location, their dog’s name, and other publicly available information, and it generates a few tens of thousands of potential passwords for every one of those details.
This should give you an understanding on how fast passwords can get compromised."
Alex "Jay" Balan (Director of Security Research, Bitdefender)
Steps to Take When Your Password is Exposed in a Data Breach
Data breaches can happen all the time and they impact almost everyone. This is why it is important to recognize that once your information is leaked, it cannot be retrieved, erased or completely removed from the Internet.
Your best chance to minimize your exposure is to:
- Enable two-factor authentication - Having another layer of authorization in place can stop cyber-criminals from taking over your accounts, once they steal your passwords.
- Start using a password manager - By using a multi-platform service like Bitdefender Password Manager you can add passwords into your secure vault and change them to longer, more complex variants that cannot be easily cracked.
- Stay informed with real-time alerts - With Bitdefender Digital Identity Protection you can get alerted if your personal information is exposed in a data breach.
Pasword Length and Complexity are Key Security Factors
It comes as no surprise that a password such as 'password123' can be instantly cracked, as it is one of the world's most commonly used.
How about a password like 'vqcV#Ru4UgWe^!4Qpz4Q*N4PzswCoWiubvV' randomly generated by a password manager? Cracking this would take years and require substantial computing resources.
Yes, it’s impossible to memorize – because you are not supposed to. Your password manager does that for you, for all your accounts, across your devices. All you need to remember is your master password, which is basically the key to your vault. The password manager then auto-fills your credentials, saving time and significantly boosting your security.
Additionally, this service offers guidance on improving weak passwords, alerting you to possible vulnerabilities.
Guidelines for Choosing a Truly Secure Password
Here’s a three-part answer to the million-dollar question: what password is most secure?
A secure password:
- is over 30 characters long
- combines lowercase and uppercase letters, numbers, and symbols
- is truly random (generated by a trustworthy password manager)
Keep in mind: passwords that are too easy to memorize are often vulnerable and susceptible to being cracked.
"We have been using passwords for the last 40 years and everybody knows that they're an outdated technology. They haven't aged well.
So the only way we can still enjoy our privacy and retain control over our accounts is to increase the complexity of passwords. We have reached a threshold where memorizing passwords is no longer viable, if you don't want these passwords to get immediately cracked.
The only viable way to use passwords is to store them in a password manager which is a must-have, given the performance of home computing or computer clusters that can run through passwords until they crack them."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Are Password Managers Safe? Let's Find Out
Just like any other online privacy and security products, it all depends on the company that develops and maintains the solution. A password manager is only as trustworthy as the company that builds it.
A reliable company will have multiple independent sources that validate their products and services. Independent tests run by established domain authorities, well-documented support knowledge bases, a track record of prompt responses and action when a vulnerability appears – these are the factors that show you can trust a company with your most sensitive information.
"Back when passwords became increasingly common when signing up for services, database operators had to deal with storing that information in plain text.
What that meant was that the password in the database was compared with what the user entered before they pressed the login button. If those two passwords matched, then they were allowed in.
One major flaw with this mechanism was that whoever got into the database, also got access to everyone’s passwords.
The solution was a technique that's called hashing. This one-way mechanism basically means turning a password into a ‘fingerprint’. That ‘fingerprint’ cannot be reversed back to the original password – at least in theory – unless you brute force it by going through all the possible key combinations until you get to the same hash at the other end."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Are Password Managers Worth Using?
The main advantages of using a password management service include:
- Managing numerous passwords effortlessly while remembering just one (your master password)
- The ability to generate longer, more complex, and significantly secure passwords
- Substantial time-saving with the autofill feature accross devices
How About Storing Passwords in Web Browsers?
Storing your passwords in your browser is better than nothing, if it helps you set stronger, more complex ones. However, it does not offer the same protection and ease of use as a password manager. Here’s why.
First, lack of mobility. To use the passwords stored in your browser, you will need to copy and paste them into other apps.
Secondly, you must create an account to configure the browser, so that you can access your passwords on other devices.
Lastly, another significant concern with storing passwords in your browser is they are often targets for cyber-attacks. As they play such an important role in your online interactions, this means your entire browsing history can also be exposed.
"A browser usually undergoes a lot of scrutiny from cyber criminals, so they are adept at employing the best coding standards of industry protocols around securing safe information. I’d say password managers in browsers are way better than writing passwords down or memorizing them, but not as good as a dedicated password management solution."
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Until the Internet becomes a fully passwordless environment, you can still take informed actions based on the expert advice about password security.
Thorough research for a trustworthy password manager, combined with constant monitoring of your ever-growing digital footprint, will empower you to take decisive steps towards protecting your online privacy.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts
